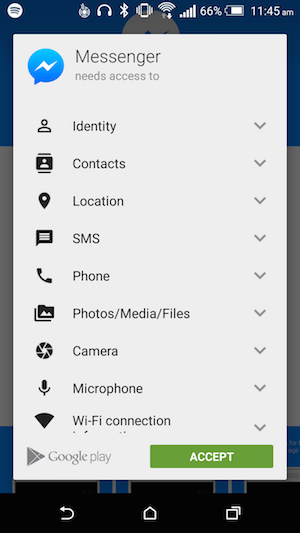
Mobile applications increasingly want access to various functions on your smartphones and tablets, such as your location and contacts book. But some of these app permissions should not be granted.App Store, Google Play and Windows Phone store users will know by now that, when installing an app or using a particular feature for the first time, the app will ask their permission to access certain features of the device. For example, a map application will ask for access to the GPS, while VoIP and other voice-calling applications may require access to the phone and device ID.
Read on, source: What app permissions should I be wary of?